Take Time to See the Signs
International Fraud Awareness Week is November 17-23
How to Spot a Phishing Email: an article by Luke Irwin
Email phishing is one of the most frequent forms of cybercrime, but despite how much we think we know about these scams, they still catch us far too often.
According to Proofpoint’s State of the Phish Report, 83% of organizations fell victim to a phishing attack last year.
Meanwhile, a Verizon Data Breach Investigations Report found that 25% of all data breaches involve phishing.
These figures help explain why phishing is considered to be among the biggest cyber security risks that organizations face. With a single email, criminal hackers can steal our personal information or infect our devices with malware.
Fortunately, preventing these attacks can be as simple as knowing how to identify phishing emails. But how do you spot a scam email? Here are five real-life examples to demonstrate the common signs that someone is trying to scam you.
1. The message is sent from a public email domain
No legitimate organization will send emails from an address that ends ‘@gmail.com’. Not even Google. Except for some small operations, most companies will have their own email domain and email accounts. For example, genuine emails from Google will read ‘@google.com’. If the domain name (the bit after the @ symbol) matches the apparent sender of the email, the message is probably legitimate. By contrast, if the email comes from an address that isn’t affiliated with the apparent sender, it’s almost certainly a scam. The most obvious way to spot a bogus email is if the sender uses a public email domain, such as ‘@gmail.com’.
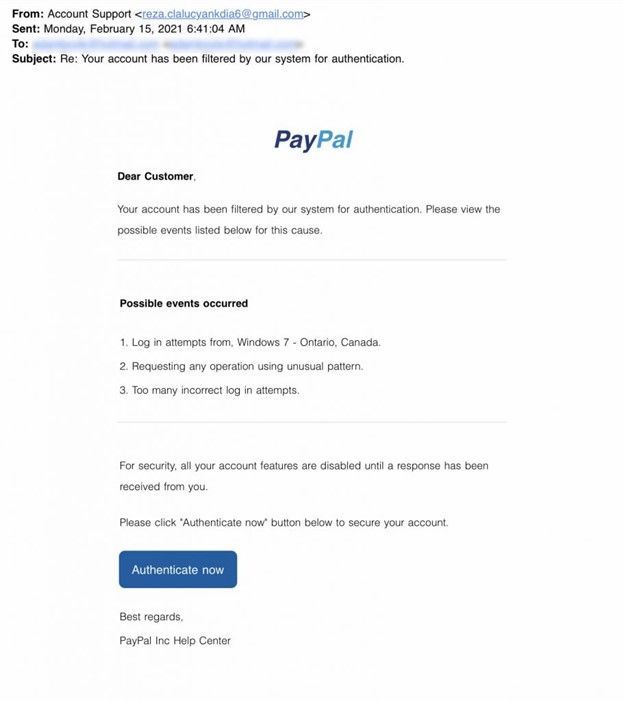
In the following example, you can see that the sender’s email address doesn’t align with the message’s content, which appears to be from PayPal. However, the message itself looks realistic, and the attacker has customized the sender’s name field so that it will appear in recipients’ inboxes as ‘Account Support’.
Other phishing emails will take a more sophisticated approach by including the organization’s name in the local part of the domain. The address might read ‘paypalsupport@gmail.com’ for example. At first glance, you might see the word ‘PayPal’ in the email address and assume it is legitimate. However, you should remember that the important part of the address is what comes after the @ symbol. This dictates the organization from which the email has been sent.
If the email is from ‘@gmail.com’ or another public domain, you can be sure it has come from a personal account.
2. The domain name is misspelled.
There’s another clue hidden in domain names that provides a strong indication of phishing scams – unfortunately, it complicates our previous clue.
Anyone can buy a domain name from a registrar. And although every domain name must be unique, there are plenty of ways to create addresses that are indistinguishable from the one that’s being spoofed.
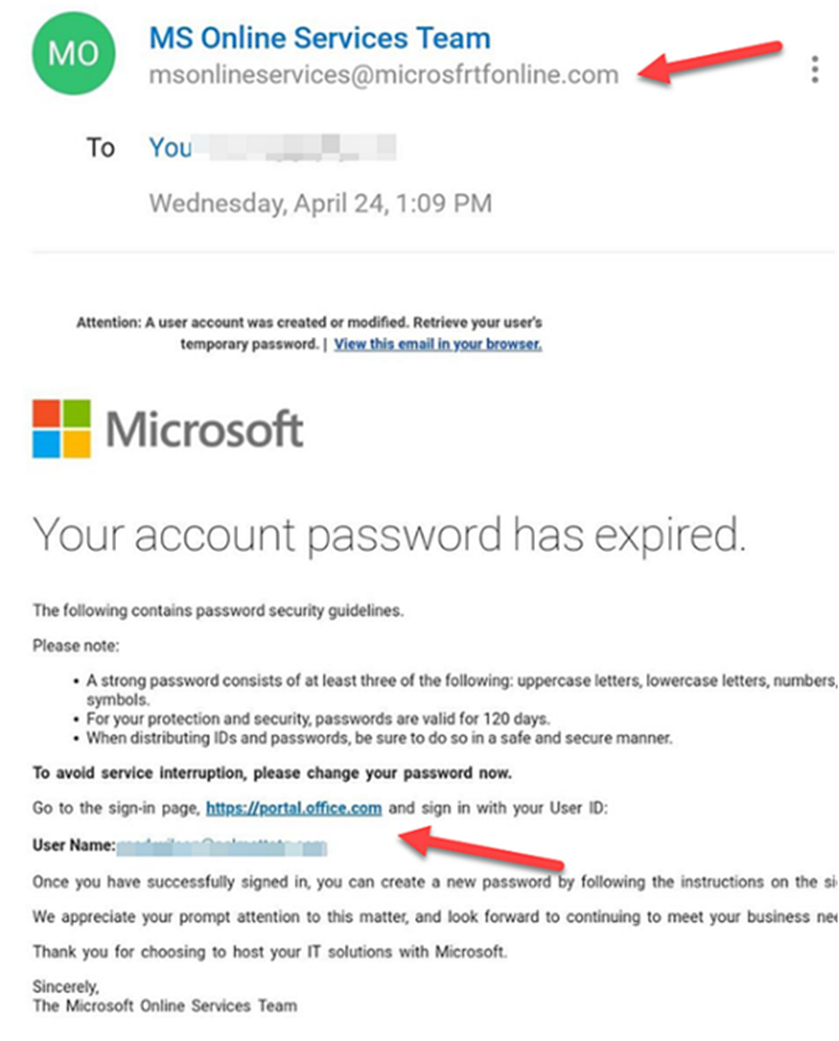
In the next example, scammers have registered the domain ‘microsfrtfonline.com’, which to a casual reader mimics the words ‘Microsoft Online’, which could reasonably be considered a legitimate address.
Remember, criminal hackers only require one mistake from one employee for their operation to be a success. Everyone in your organization must be confident in their ability to spot a scam upon first seeing it.
3. The email is poorly written
You can often tell if an email is a scam if it contains poor spelling and grammar. Many people will tell you that such errors are part of a ‘filtering system’ in which cyber criminals target only the most gullible people. The theory is that if someone ignores clues about how the message is written, they’re less likely to pick up clues during the scammer’s endgame. However, this only applies to outlandish schemes like the oft-mocked Nigerian prince scam, to which you must be incredibly naive to fall victim.
That, and scams like it, are manually operated: once someone takes to the bait, the scammer has to reply. As such, it benefits the crooks to ensure the pool of respondents contains only those who might believe the rest of the con.
But this doesn’t apply to phishing.
With phishing, scammers don’t need to monitor inboxes and send tailored responses. They simply dump thousands of crafted messages on unsuspecting people. As such, there’s no need to filter out potential respondents. So why are many phishing emails poorly written? In this case, the most obvious answer is the correct one: the scammers aren’t very good at writing. Remember, many of them are from non-English-speaking countries and backgrounds where they will have limited access or opportunity to learn the language. With this in mind, it becomes much easier to spot the difference between a typo made by a legitimate sender and a scam.
When crafting phishing messages, scammers often use a spellchecker or translation machine, giving them all the right words but not necessarily in the proper context. Take the following example of a scam imitating Windows.
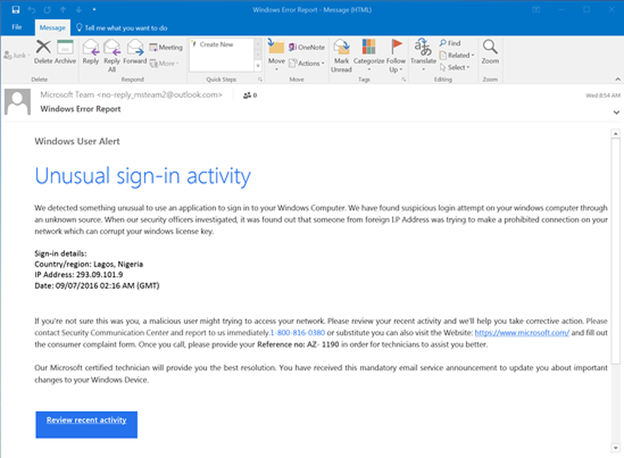
No individual word is misspelled, but the message contains grammatical errors that a native speaker wouldn’t make, such as “We detected something unusual to use an application”. Likewise, there are strings of missed words, such as “a malicious user might trying to access” and “Please contact Security Communication Center”. These are consistent with the kinds of mistakes people make when learning English. Any supposedly official message written this way is almost certainly a scam. That’s not to say any email with a mistake is a scam, however. Everyone makes typos from time to time, especially when they’re in a hurry. It’s, therefore, the recipient’s responsibility to look at the context of the error and determine whether it’s a clue to something more sinister. You can do this by asking:
- Is it a common sign of a typo (like hitting an adjacent key)?
- Is it a mistake a native speaker shouldn’t make (grammatical incoherence, words used in the wrong context)?
- Is this email a template which should have been crafted and copy-edited?
- Is it consistent with previous messages I’ve received from this person?
If you’re in any doubt, look for other clues that we’ve listed here or contact the sender using another line of communication, whether in person, by phone, via their website, an alternative email address or through an instant message client.
4. It includes suspicious attachments or links
Phishing emails come in many forms. We’ve focused on emails in this article, but you might also get scam text messages, phone calls or social media posts. But no matter how phishing emails are delivered, they all contain a payload. This will either be an infected attachment you’re asked to download or a link to a bogus website. The purpose of these payloads is to capture sensitive information, such as login credentials, credit card details, phone numbers and account numbers.
Infected attachments
An infected attachment is a seemingly benign document that contains malware.
In a typical example, like the next one, the phisher claims to be sending an invoice. It doesn’t matter whether the recipient expects to receive an invoice from this person or not because, in most cases, they won’t be sure what the message pertains to until they open the attachment. When they open the attachment, they’ll see that the invoice isn’t intended for them, but it will be too late. The document unleashes malware on the victim’s computer, which could perform any number of nefarious activities. It's advised that you never open an attachment unless you are confident that the message is from a legitimate party. Even then, you should look out for anything suspicious in the attachment. For example, if you receive a pop-up warning about the file’s legitimacy or the application asks you to adjust your settings, then don’t proceed. Contact the sender through an alternative means of communication and ask them to verify that it’s legitimate.

Suspicious links
You can spot a suspicious link if the destination address doesn’t match the context of the rest of the email.
For example, if you receive an email from Netflix, you would expect the link to direct you towards an address that begins ‘netflix.com’. Unfortunately, many legitimate and scam emails hide the destination address in a button, so it’s not immediately apparent where the link goes.
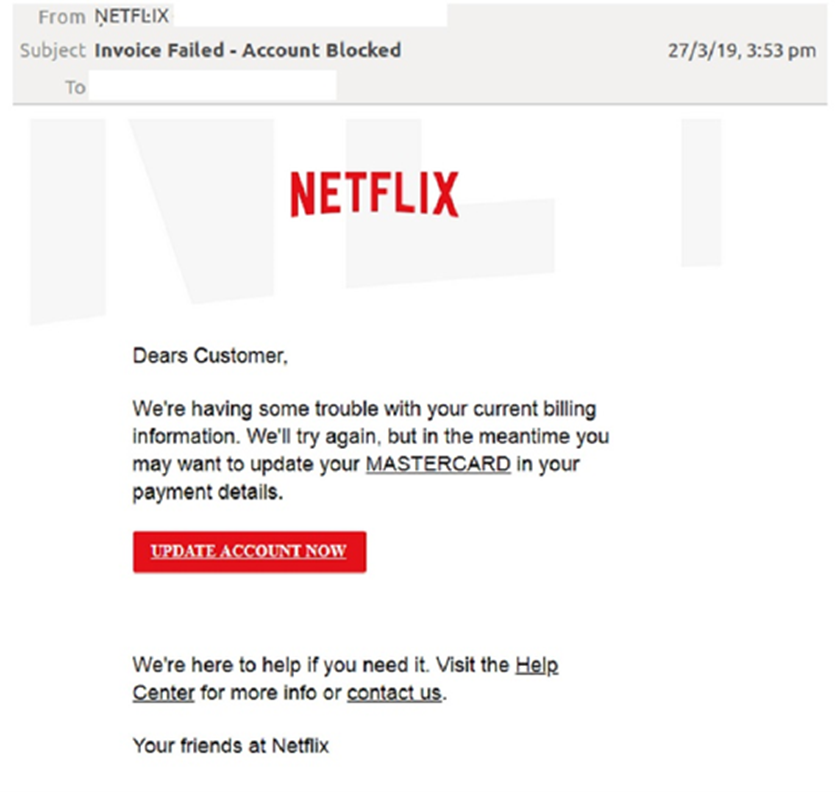
In this next example, the scammers are claiming that there is an issue with the recipient’s Netflix subscription. The email is designed to direct them to a mock-up of Netflix’s website, where they will be prompted to enter their payment details.
The fraudsters achieve two things by including the link within a button that says ‘Update account now’.
First, it makes the message look genuine, with buttons becoming increasingly popular in emails and websites. But more importantly, it hides the destination address, making it a hyperlink.
To ensure you don’t fall for schemes like this, you must train yourself to check where links go before opening them.
Thankfully, this is straightforward: on a computer, hover your mouse over the link, and the destination address appears in a small bar along the bottom of the browser.
On a mobile device, hold down on the link, and a pop-up will appear containing the link.
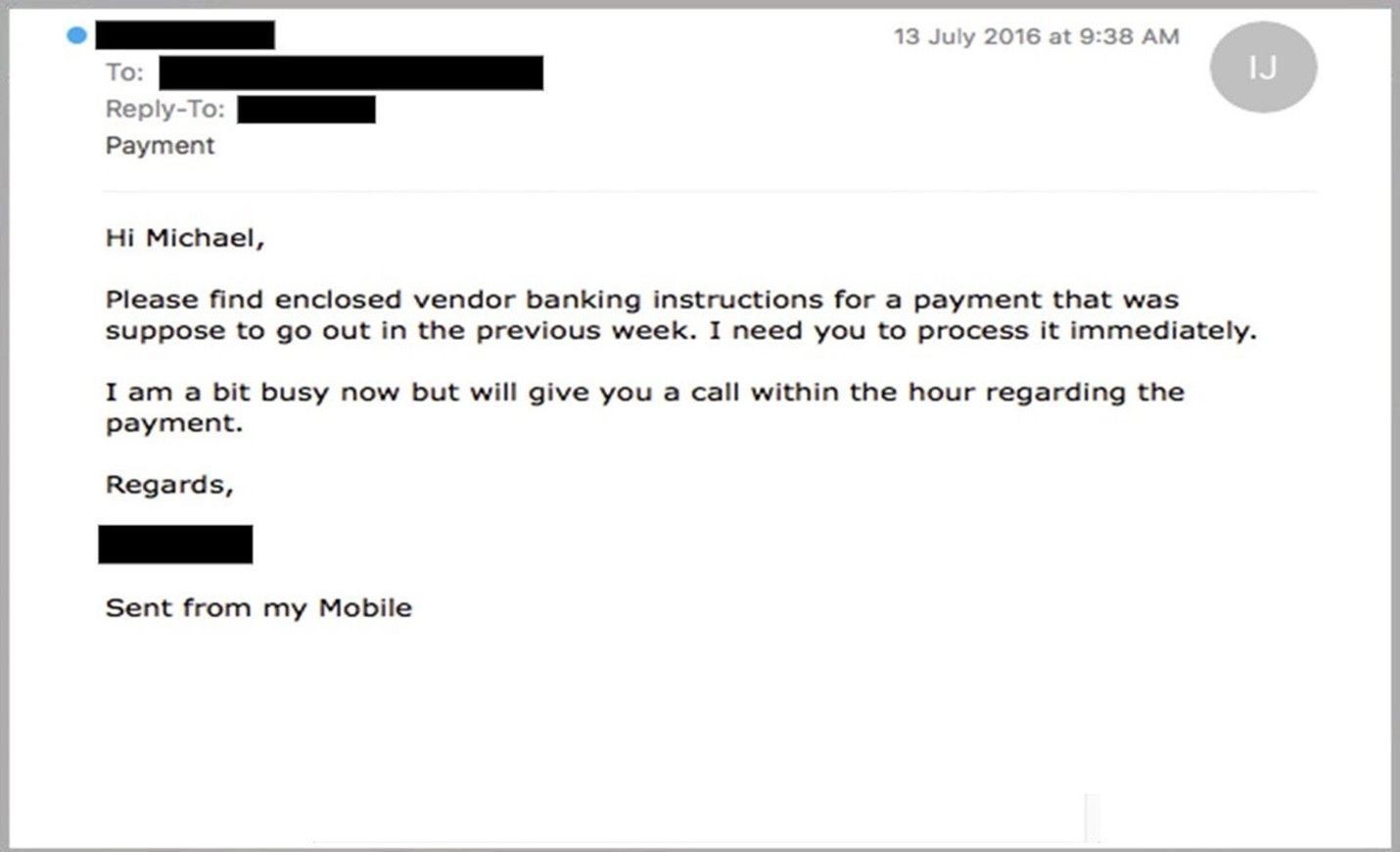
5. The message creates a sense of urgency
Scammers know that most of us procrastinate. We receive an email giving us important news, and we decide we’ll deal with it later. But the longer you think about something, the more likely you will notice things that don’t seem right.
Maybe you realize that the organization doesn’t contact you by that email address, or you speak to a colleague and learn that they didn’t send you a document. Even if you don’t get that ‘a-ha’ moment, returning to the message with a fresh set of eyes might help reveal its true nature. That’s why so many scams request that you act now, or else it will be too late. This has been evident in every example we’ve used so far. PayPal, Windows and Netflix provide regularly used services, and any problems with those statements could cause immediate inconveniences.
The manufactured sense of urgency is equally effective in workplace scams. Criminals know that we’re likely to drop everything if our boss emails us with a vital request, especially when other senior colleagues are supposedly waiting on us. Phishing scams like this are particularly dangerous because, even if the recipient did suspect foul play, they might be too afraid to confront their boss. After all, if they are wrong, they’re implying that there was something unprofessional about the boss’s request. However, organizations that value cyber security would accept that it’s better to be safe than sorry and perhaps even congratulate the employee for their caution.
The best way to protect yourself and your business from phishing scams is to become educated on how they work and what to look out for.




